Security
Security
Our Philosophy: You Hold The Keys
Security, along with privacy and freedom, is a core principle that defines everything Purism does. Most vendors design security solutions that anchor all trust in the vendor, remove control and keys from the customer. Vendors do this to make the customer wholly dependent upon the vendor for their security. Purism rejects this philosophy and instead designs security solutions that empower the customer.
With Purism, you hold the keys.
We believe that freedom is essential to security. Our commitment both to user freedom and software freedom means we can deliver advanced security measures other vendors can’t. We also think security should be convenient and hardware and software should be secure by default. Our approach results in a completely unique combination of security solutions you simply can’t find anywhere else.
Hardware Kill Switches

A defining feature of Purism Librem laptops and the Librem 5 phone is the addition of hardware kill switches. Instead of just disabling hardware with software, the two hardware kill switches in our Librem laptops physically disable the webcam and microphone, and the WiFi card respectively.
Our Librem 14 also disables the microphone in the headphone jack, and adds an additional hardware kill switch on the motherboard to write-protect the BIOS and EC firmware.
The Librem 5 phone has hardware kill switches that disable the cameras and microphone, and WiFi and Bluetooth hardware, but it also adds a third kill switch that disables the cellular modem. You can use all three kill switches to enter “Lockdown mode” which disables all other sensors on the device including GPS, accelerometer, proximity sensors, and light sensors.

Secure Software Supply Chain
Supply chain security has started to be a hot topic in the security world, for good reason; You cannot get better supply chain security than with free software. This article describes all of the steps we take to secure the software supply chain starting with our firmware and extending to our operating system and every piece of software we run.
Purism has a great advantage over other vendors when it comes to protecting the software supply chain. We can offer a 100% free software operating system, PureOS, on our laptops. By only installing free software on our laptops, all of the source code in the operating system can be audited by anyone for backdoors or other malicious code. Beyond that, all of the software within PureOS is signed and those signatures are verified every time you install new software or update existing software.
Unlike proprietary software, we can also address the risk from an attacker who can inject malicious code somewhere in the build process before it’s signed. With Reproducible Builds you can download the source code used to build your software, build it yourself, and compare your output with the output you get from a vendor. If the output matches, you can be assured that no malicious code was injected somewhere in the software supply chain and it 100% matches the public code that can be audited for back doors. Proprietary software can’t be reproducibly built by third parties (because they don’t share the code), you are left relying on the package signature for all your supply chain security. We are working to ensure all of the software within PureOS can be reproducibly built and to provide you tools to audit our work.
Tamper Evident Boot Firmware
Security must be anchored in trust that starts the moment you power on the computer. We offer PureBoot to secure the boot process, which comprises a number of different technologies:
- Neutralized and Disabled Intel Management Engine
- The coreboot free software BIOS replacement
- A Trusted Platform Module (TPM) chip
- Heads, our tamper-evident boot software that loads from within coreboot
- Librem Key, our USB security token
- Multi-factor authentication that unlocks disk encryption using the Librem Key
You can read more about how these components fit together to protect the entire boot process here, and customers can upgrade to the PureBoot Bundle when ordering a laptop or PC and have PureBoot set up by us at the factory.
Anti-interdiction Services
We also offer a solution for customers who are concerned about their computer being intercepted and tampered with; Between the time it leaves our fulfillment center and the time they receive and open the box. Our anti-interdiction service is an upgrade to the PureBoot Bundle and offers a high-touch, secure process that is custom-tailored based on a particular customer’s threats. We’ve found the anti-interdiction service to be popular both for people who face extreme threats, as well as people who just want the peace of mind that their computer has not been tampered with in shipment.

A close-up of the unique pattern of blue glitter nail polish on the center screw.
Secure Hardware Supply Chain
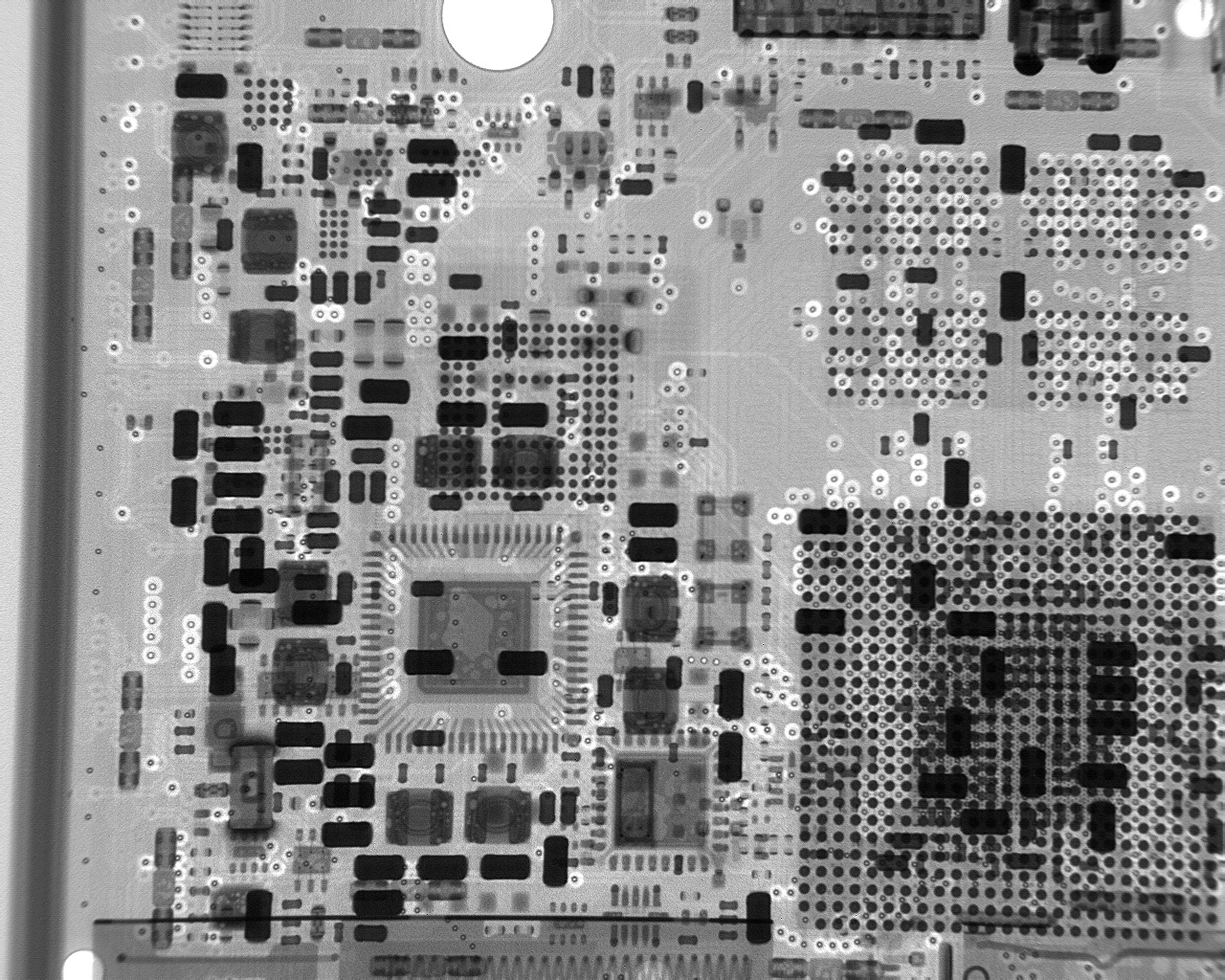
We continue to expand products and features for customers who are concerned about hardware supply chain security. We manufacture our Librem Key in the USA and offer the Librem 5 USA as a premium version of our standard Librem 5 phone but with made in USA electronics. For our Librem 5 we also release schematics as well as X-rays so customers can audit their hardware.
Security Contact and Disclosures
If you have discovered a security issue in our hardware, software, or services, contact support@puri.sm.
If you want to send a GPG-encrypted email, you can find the GPG public key for support@puri.sm here.
Our Secure Products
We believe people should have secure devices that protect them rather than exploit them. To that purpose, we provide everything you need in a convenient hardware and software product. We offer high-quality hardware and software with a focus on privacy, security, and freedom.

