Coreboot News: New Script, Pre-built Binaries and PureBoot on Non-TPM Laptops
Things have been busy in the coreboot department, lately, and we are excited to announce a number of new improvements:
- Pre-built binaries of our default coreboot BIOS firmware
- Pre-built binaries of our tamper-evident PureBoot firmware
- Improved script to automate coreboot builds and flashing from pre-built binaries
- PureBoot tamper-evident support for non-TPM Librem 13 version 2 and Librem 15 version 3 systems
Pre-built Binaries
In the past, updating to our latest coreboot BIOS images required you to go through an automated, yet time-consuming process, of downloading and compiling coreboot from scratch. While we know that many people prefer building the firmware from source–after all that’s one of the big advantages to using free software –some would rather have the convenience of pre-built binaries, for the same reason they like pre-built binaries for regular OS packages.
This is a way of getting convenience while also knowing the ROM you are loading has already been tested for your particular laptop version. Just like with our regular coreboot BIOS, trying out our beta PureBoot firmware images–that use Heads instead of SeaBIOS–required users to go through a somewhat complicated process of building from source. While we hope to soon offer PureBoot as a pre-install option when you buy a laptop, in the mean time we will be providing pre-built PureBoot firmware binary images.
Starting today, you can get binary ROM images both for our traditional coreboot and PureBoot in the https://source.puri.sm/coreboot/releases repository. We’ve already disabled and neutralized the Intel Management Engine in these pre-built images as well. As we update and make improvements to coreboot, we will keep these images up-to-date—a great reference point if you want to make sure you are running firmware with the latest updates and security improvements.
Improved Flashing Script
Providing pre-built images is a good start to making our coreboot images easier to install and update, but we do realize most people don’t want to figure out how to use flashrom on the command line, and we are releasing a new and improved flashing script at https://source.puri.sm/coreboot/utility so it’s easier to either pull down the latest pre-built coreboot binary, or build it yourself. If you are using the traditional coreboot BIOS, it will even flash the update for you, whether you want to update the traditional SeaBIOS coreboot image or transition over to PureBoot. Current PureBoot users should flash from within the trusted Heads environment itself: the script detects it and provides users with instructions on which ROM file they should copy to a USB disk and flash.
To use the improved script, copy https://source.puri.sm/coreboot/utility/raw/master/coreboot_util.sh and run it as root. The README for the script lists what dependencies you need, and the script itself will also detect and alert you if you are missing packages it needs:
mkdir ~/updates cd ~/updates wget https://source.puri.sm/coreboot/utility/raw/master/coreboot_util.sh -O coreboot_util.sh sudo bash ./coreboot_util.sh
PureBoot Tamper-evident Support for Legacy non-TPM Laptops
We make sure our own security, and our improvements aren’t limited to those who buy our latest hardware. This is why we ported coreboot to the Librem 13 version 1 and continue to provide coreboot updates to it and other early Librem laptops. One of the things I’m most excited to announce is that we have ported PureBoot tamper-evident support into Skylake-based Librem laptops without TPM chips! This means that if you have a Librem 13 version 2 or Librem 15 version 3 without a TPM, you can now use a Librem Key in place of your TPM chip and get similar protection against tampering!
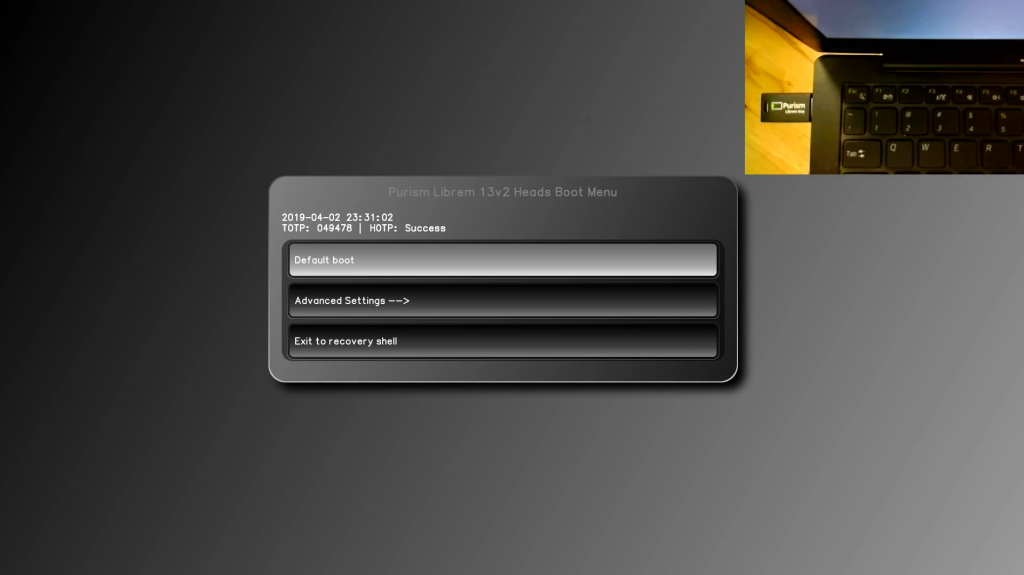
How Does This Work Without A TPM?
When we first announced our partnership with Trammell Hudson to port Heads to our laptops, we also started offering TPM chips, first as an optional upgrade for an extra cost and ultimately installed by default for no extra charge. Until now, the TPM chip was needed to store all of the pre-approved firmware measurements securely, as that was the only method Heads supported; once we announced the addition of the Librem Key to our product line, we realized that there might be a way for the Librem Key to take the place of the TPM for older Librem laptops.
Traditionally, Heads will send measurements of itself to the TPM, and if it matches the pre-approved measurements you originally set up the TPM will unlock a secret that gets converted into a 6-digit HOTP code and sent to the Librem Key, which has its own copy of the secret and generates its own 6-digit HOTP code. If the code it receives over USB matches the code it generates, it flashes a green LED; otherwise it flashes a red LED to alert you of tampering.
When configured for a system without a TPM, and instead of using a random secret that’s unlocked with the correct firmware measurement, our PureBoot Heads ROM uses the firmware measurement itself—converted to a hash—as the secret. When originally setting it up, the Librem Key is to be configured to store a copy of that secret. Upon boot, Heads uses its own local flashrom to pull down a full copy of the running firmware, hashes it, and converts it into a 6-digit HOTP code. Like before, it sends that HOTP code to the Librem Key and the Librem Key compares it with the code it generates. If they match, green LED, if they don’t, red LED.
This method turns the Librem Key into a kind of external TPM—at least in the sense that the device itself is being sent firmware measurements instead of the TPM, in the form of a hash converted into a 6-digit code. The main practical difference you’ll notice is that the no-TPM solution takes an additional number of seconds at boot, before you will get to the first boot prompt—as it takes time to copy down the full firmware image.
What’s Next for Coreboot
We are working on a number of additional improvements to make coreboot, PureBoot and our coreboot update process even better. Among them is a migration to coreboot 4.9, compiling the PureBoot firmware from source and from within our firmware update script; more automation around the initial PureBoot and Librem Key setup process, and maybe—if there’s sufficient interest—backporting PureBoot to Broadwell-based Librem laptops (13 version 1 and 15 version 2).
Recent Posts
- Trump T1 Phone Android OS vs. PureOS
- After a week, Trump Mobile drops claim that the T1 Phone is “Made in the USA”
- The 2025 Most Secure Phone in The World Reviews Are In: Efani, Analytics Insight, Navi, and Cashify
- Why Purism Manufactures Electronics in the USA
- CNN Report: Purism is the Only Known U.S. Phone Manufacturer
Related Content
- Hidden Operating Systems in Chips vs. Secure, Auditable OSes: A Cybersecurity Comparison
- Purism Releases STEP File for Librem 5
- A Secure Foundry for Government Mobile Computing Needs
- Flipping the Script: Exploring New Paradigms in Secure Mobile Computing
- Your Phone is Giving Away More Than You Ever Bargained For


