Qubes 4.0 fully working on Librem laptops, coreboot added IOMMU and TPM
Purism
Latest posts by Purism (see all)
- A Quarter Century After Cyberselfish, Big Tech Proves Borsook Right - December 20, 2025
- PureOS Crimson Development Report: November 2025 - December 15, 2025
- Purism Liberty Phone Exists vs. Delayed T1 Phone - December 10, 2025
It’s easy to take things for granted when your computer runs a non-free proprietary BIOS. While the BIOS that comes with your computer is usually configured to match its features that’s not always the case. You end up with a sort of binary arrangement: if your BIOS supports a feature or allows you to change a setting, great, but if it doesn’t, you are generally out of luck. One example is with some of the new UEFI computers that ship with stripped-down BIOS options. One example we ran across recently had legacy boot disabled, secure boot enabled, and no way to change either setting, which is a terrible restriction for users wanting a free software distribution like PureOS or any another distribution that avoids the misnamed “secure boot” UEFI option.
From the beginning our goal has been to ship ethical computers without any proprietary code and the BIOS was one of our first targets. Starting last summer, all our computers come with the Free/Libre and Open Source coreboot BIOS. In addition to the many ethical and security advantages behind shipping an ethical BIOS/firmware, another advantage we have is that if our coreboot image doesn’t support a feature today, that doesn’t mean it won’t tomorrow.
We are happy to announce that due to the hard work of Youness “KaKaRoTo” Alaoui and Matt “Mr. Chromebox” DeVillier we have added IOMMU and TPM support to our new coreboot 4.7 BIOS. I’ve tested this personally on a Librem 13v2 with the latest Qubes 4.0-rc4 installer and the install completes with no warnings and reboots into a functional Qubes 4 desktop with working sys-net and sys-usb HVM VMs. In this blog post I’ll go over these different features, what they are, and why they are important.
IOU one IOMMU
As we started shipping coreboot-enabled Librem laptops, we received feedback from some customers that when they installed the early release candidates of Qubes 4.0, the installer complained that the system didn’t support IOMMU. IOMMU (Input-Output Memory Management Unit, also known as VT-d in Intel processors) sits between devices and the physical memory on a system and presents virtual memory addresses to devices that want Direct Memory Access (DMA) such as PCI devices. It turns out that while coreboot does support IOMMU for some CPUs, that support hadn’t yet been ported to Skylake processors.
IOMMU is a particularly useful feature for virtualization as it allows a virtual host DMA features while protecting the memory of other VMs. This isolation feature is important to Qubes because Qubes attaches untrusted devices like USB controllers and network cards that normally require DMA access to untrusted VMs. With IOMMU, Qubes can protect the memory of trusted VMs from malicious DMA attacks on devices attached to untrusted VMs.
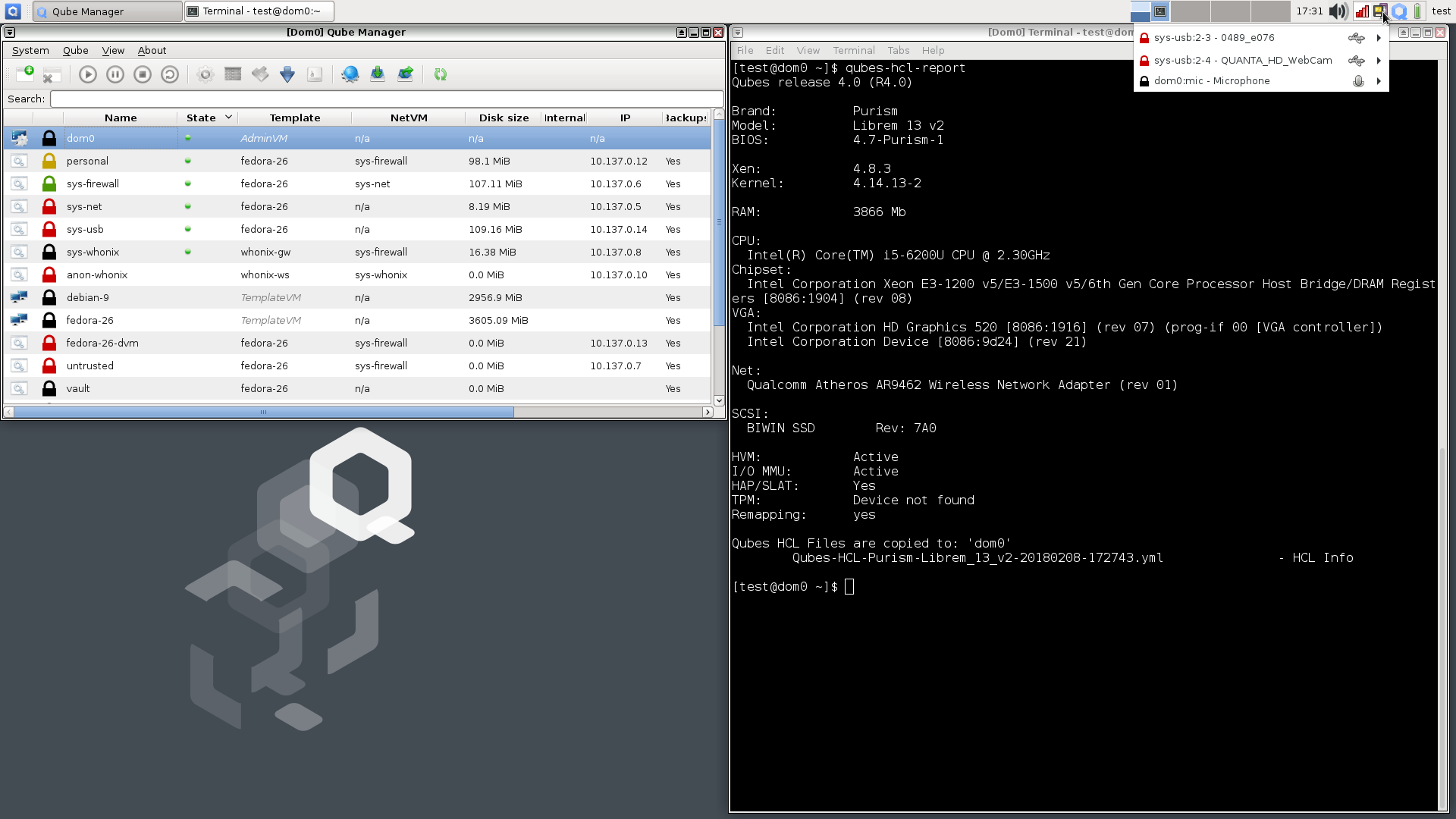
Starting with Qubes 4.0, the installer will warn users if their computers do not support certain CPU features such as IOMMU. While you can ignore the warning and complete the install, certain VMs with PCI devices attached such as sys-net and sys-usb will not start unless you change their virtualization mode from HVM to PV, bypassing the protections IOMMU provides. Up until now, this was the workaround for Librem 13v2 and 15v3 laptops as well… but with the latest coreboot image you can now install without any warnings, and HVM sys-net and sys-usb VMs will be able to start without issue:
Initial TPM support in our coreboot images
Late last year we announced that we are offering TPM (Trusted Platform Module) as an add-on upgrade to Librem laptops. The TPM acts as a kind of Hardware Security Module and lets you store keys and perform basic operations with those keys without the keys ever leaving the TPM itself. Our plan is to use the TPM with Heads to provide tamper-proofing against malware that might try to compromise the BIOS, boot loader, or kernel.
We have started shipping Librem laptops with TPM and behind the scenes have also been working to add support to our coreboot image. If you recently received a TPM-enabled Librem laptop and looked in dmesg output or ran a tool like tpm_version it would appear that the TPM didn’t get installed. Don’t worry–once you update coreboot the output will look more like this (taken from my Librem 13v2 TPM):
$ tpm_version TPM 1.2 Version Info: Chip Version: 1.2.4.40 Spec Level: 2 Errata Revision: 3 TPM Vendor ID: IFX Vendor Specific data: 04280077 0074706d 3631ffff ff TPM Version: 01010000 Manufacturer Info: 49465800
Coreboot and Qubes 4.0 Availability
We are now finishing testing on our new coreboot image and will start including it on all new laptop shipments so if you were holding off on getting a Librem laptop until it worked well with Qubes 4.0 you don’t need to wait any longer.
For existing customers, we will follow up with a new blog post that walks you through how to update coreboot to the latest version step-by-step.
We have long provided Qubes 3.2 install disks as an option when ordering our Librem laptops but recently we have been asked why we don’t provide Qubes 4.0 instead. Right now we ship Qubes 3.2 because it’s the current stable Qubes release. If you have followed the Qubes 4.0 release candidates you know that a lot has changed behind the scenes and up until recently the release candidates still had some bugs and features to work out. With 4.0-rc4, however, it looks like things are starting to stabilize, backup/restore from Qubes 3.2 works reasonably well, and even the “Qube VM Manager” GUI program is back so it is likely that a stable 4.0 release will ship soon. Once it ships and we confirm it works as well on our hardware as 4.0-rc4 does, we will offer it as an option in place of Qubes 3.2 on our order page.
What’s Next
Now that we have a coreboot image that works well with Qubes 4, our next step will be to update the Qubes HCL (Hardware Compatibility List) for our current product line. For those that are curious, here’s the Qubes 4.0-rc4 qubes-hcl-report output from my Librem 13v2 laptop without TPM (the kind that many of our existing customers have):
--- layout: 'hcl' type: 'laptop' hvm: 'yes' iommu: 'yes' slat: 'yes' tpm: 'unknown' remap: 'yes' brand: | Purism model: | Librem 13 v2 bios: | 4.7-Purism-1 cpu: | Intel(R) Core(TM) i5-6200U CPU @ 2.30GHz cpu-short: | FIXME chipset: | Intel Corporation Xeon E3-1200 v5/E3-1500 v5/6th Gen Core Processor Host Bridge/DRAM Registers [8086:1904] (rev 08) chipset-short: | FIXME gpu: | Intel Corporation HD Graphics 520 [8086:1916] (rev 07) (prog-if 00 [VGA controller]) Intel Corporation Device [8086:9d24] (rev 21) gpu-short: | FIXME network: | Qualcomm Atheros AR9462 Wireless Network Adapter (rev 01) memory: | 3866 scsi: | BIWIN SSD Rev: 7A0 usb: | 1 versions: - works: 'FIXME:yes|no|partial' qubes: | R4.0 xen: | 4.8.3 kernel: | 4.14.13-2 remark: | FIXME credit: | FIXAUTHOR link: | FIXLINK ---
Now that TPM-enabled laptops are shipping and we have it enabled in coreboot, the next major area of focus in coreboot itself is going to be around integration with Heads. We hope to have an update along those lines soon. Also, since we continue to be able to provide extra features to our customers through coreboot updates, we are working on making the update process itself smoother.
Recent Posts
Related Content
- Code is Power!
- PureBoot Not Vulnerable to UEFI Exploits (Again)
- Intel AX200 Wi-Fi/Bluetooth Shipping for New Orders
- Librem 11 Memory Adventures
- PureBoot Framebuffer Boot Support


