Spotlight on PureBoot Restricted Boot
Purism
Latest posts by Purism (see all)
- A Quarter Century After Cyberselfish, Big Tech Proves Borsook Right - December 20, 2025
- PureOS Crimson Development Report: November 2025 - December 15, 2025
- Purism Liberty Phone Exists vs. Delayed T1 Phone - December 10, 2025
Most Big Tech efforts to secure the boot process give the vendor control over what software you are allowed to boot on your laptop, with keys they control.
With PureBoot Restricted Boot, you can lock down your boot firmware to only boot trusted, signed executables both on a local disk and USB, so you control the keys. Let’s see how you tighten down your boot security with Restricted PureBoot in this video.
Restricted Boot is disabled by default to give you maximum flexibility in what OSes you can boot, but once you enable it, an attacker can’t disable it without triggering a tamper warning.
Update to A Newer Version of PureBoot
To enable restricted boot, ensure you’re running at least version 23 of PureBoot. If you need to upgrade, follow along with this video.
Upgrade Pureboot
For those running an older version of PureBoot:
- Download the new PureBoot ROM from our release repository for your corresponding hardware.
- Copy that to a USB thumb drive and attach it to your Librem device.
- Power on your Librem and head into the PureBoot settings by pressing the escape key.
- Head to
Options->Flash or update the BIOS->Flash the firmware with a new ROM and retain BIOS settings. - Next, select your USB device, then select the ROM file.
- Select “yes” to proceed.
- Your BIOS will update and your computer will reboot once done.
Moving from Coreboot to Pureboot
If you’re currently running coreboot, you can use this utility to flash the firmware. To use it open a terminal and run these commands:
mkdir ~/updates cd ~/updates wget https://source.puri.sm/coreboot/utility/raw/master/coreboot_util.sh -O coreboot_util.sh sudo bash ./coreboot_util.sh
- Enter your root password then enter a 1 to select “Update firmware using pre-built image”
- The script will prompt you for your device model; enter your device’s corresponding number.
- Next, select PureBoot as the firmware to be flashed.
- If asked to update the serial number, the default option to extract is fine.
- Once flashed you’ll need to attach your Librem key, reboot, and follow the setup guide.
Have a look at this video for a deep dive into how the Librem Key works with PureBoot, or continue on to enable PureBoot restricted boot.
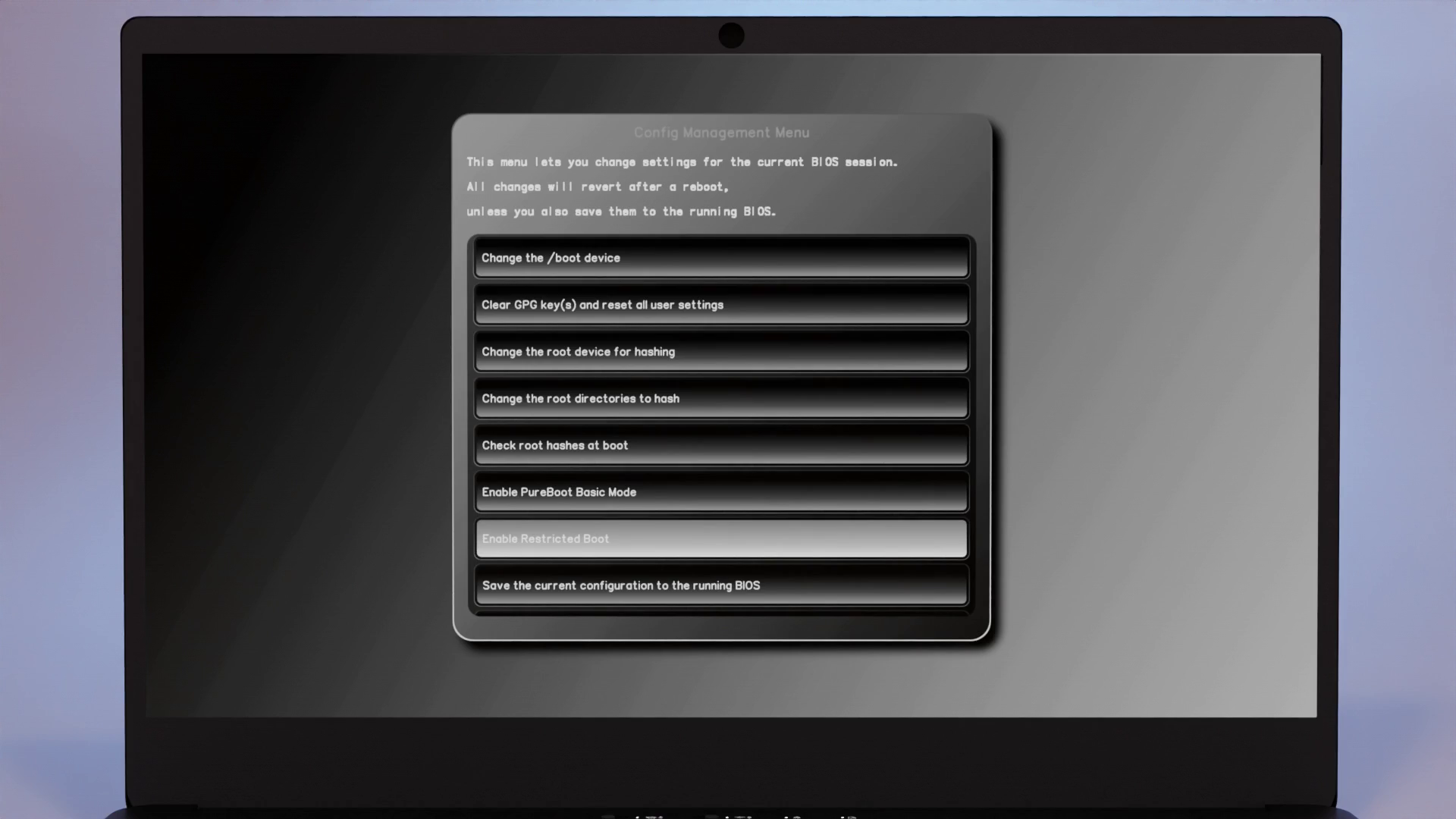
Enabling Restricted Boot
With the latest Pureboot installed, head to Options -> Change Configuration Settings -> Enable Restricted Boot.
Then, select Save changes to the running BIOS
 After rebooting, you can still boot into your system as normal, but you’ll no longer be allowed to ignore any tamper warnings and boot into failsafe mode. This also disables options like the recovery shell.
After rebooting, you can still boot into your system as normal, but you’ll no longer be allowed to ignore any tamper warnings and boot into failsafe mode. This also disables options like the recovery shell.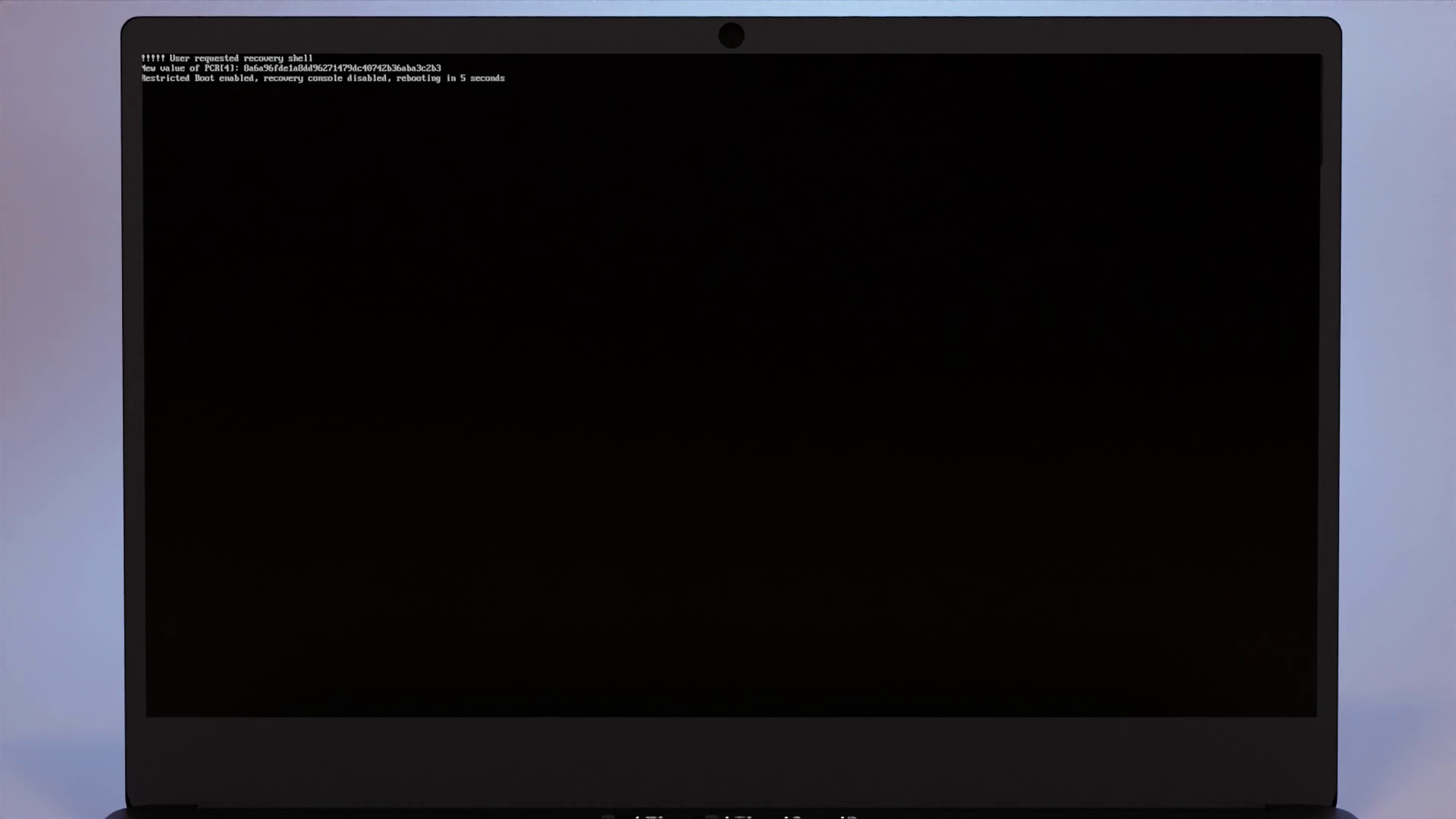 In this mode, your computer will outright refuse to boot when your boot files aren’t signed with your paired Librem Key.
In this mode, your computer will outright refuse to boot when your boot files aren’t signed with your paired Librem Key.
Updates
During normal use, when you update your OS while Restricted Boot is enabled, it will behave much like you expect. If your kernel changes, you will be prompted to re-sign files in /boot using your Librem Key and once you do, you will be able to boot into your OS as normal.
USB
In this mode, you can also boot pre-approved signed distros via USB. Instead of imaging directly to a USB, copy the ISO and the corresponding .asc GPG signature file the vendor provides. This will allow you to boot from ISOs on USB disks, as long as their signature matches one of the trusted public keys in PureBoots ISO keyring. By default, we include public keys for Arch Linux, Qubes, Tails, and PureOS. Later on, we’d like to add a feature that lets you modify the approved keys from within the GUI itself, but that feature didn’t make it for this first release.
Disabling
To disable Restricted boot, go back to Options -> Change Configuration Settings and select Disable Restricted Boot
To prevent someone from disabling this without detection, once you select this option, your TPM will be reset.
This will notify the proper user of tampering once they try to boot their computer again.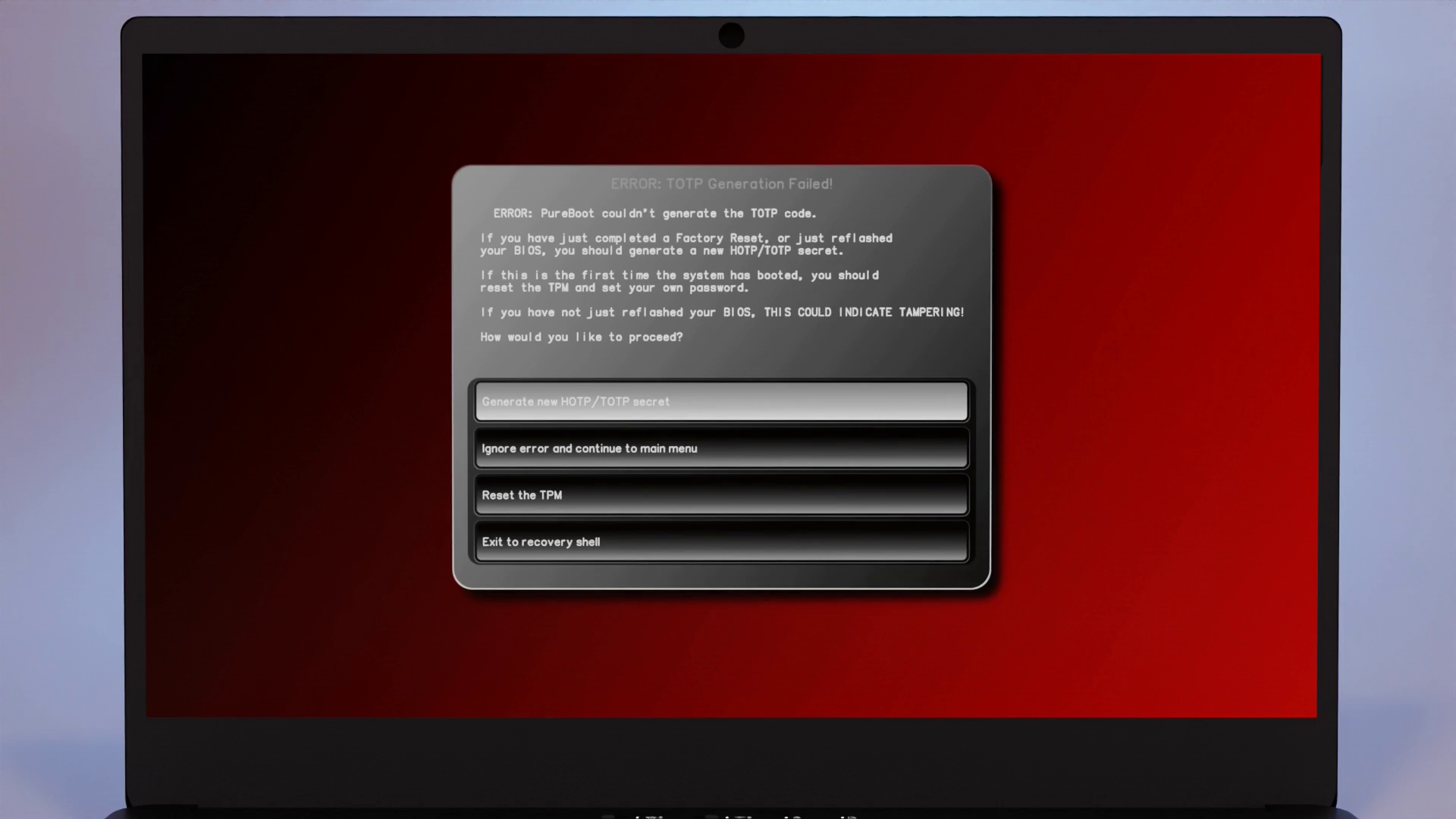
Summary
PureBoot provides flexible security measures, with defaults that balance security with ease of use. Restricted Boot allows you to tighten down boot security even further, while still having full control over your own system.
Purism Products and Availability Chart
| Model | Status | Lead Time | ||
|---|---|---|---|---|
 | Librem Key (Made in USA) | In Stock ($59+) | 10 business days | |
 | Liberty Phone (Made in USA Electronics) | In Stock ($1,999+) 4GB/128GB | 10 business days | |
 | Librem 5 | In Stock ($799+) 3GB/32GB | 10 business days | |
 | Librem 11 | In Stock ($999+) 8GB/1TB | 6+ weeks | |
 | Librem 14 | Out of stock | New Version in Development | |
 | Librem Mini | Out of stock | New Version in Development | |
 | Librem Server | In Stock ($2,999+) | 45 business days | |
 | Librem PQC Encryptor | Available Now, contact sales@puri.sm | 90 business days | |
 | Librem PQC Comms Server | Available Now, contact sales@puri.sm | 90 business days |
Recent Posts
Related Content
- A Quarter Century After Cyberselfish, Big Tech Proves Borsook Right
- PureOS Crimson Development Report: November 2025
- PureOS Crimson Development Report: October 2025
- Landfall: A Case Study in Commercial Spyware
- Librem PQC Encryptor: Future‑Proofing Against Both SS7 and Quantum


