How to Make the Most Secure Phone
for Enterprise Businesses and Governments
Todd Weaver
PGP Fingerprint: B8CA ACEA D949 30F1 23C4 642C 23CF 2E3D 2545 14F7
Latest posts by Todd Weaver (see all)
- Closing the App Gap; Focus and Momentum - September 9, 2025
- Hardware Encrypted COMSEC Bundle by Purism - April 29, 2024
- Purism Differentiator Series, Part 14: Surveillance Capitalism - April 23, 2024
tl;dr Buy the Librem 5, and if you want US Electronic manufacturing for a secure supply chain, buy the Librem 5 USA.
Making the Most Secure Phone
Making the most secure phone takes many experts to join forces, it also takes a research and development project to consider every layer in the stack and mitigate risks from beginning to end.
The Entity Behind the Secure Phone

You need to start with a legal foundation where the company making the device is legally bound and required to adhere to advancing security, one that has proven to make design decisions that benefit owning and having complete control of the entire device, hardware to software to services. Having this legal foundation is why Purism formed as a Social Purpose Company (SPC) with Articles of Incorporation that are easy to understand and legally binding.
The Team Behind the Secure Phone
You need to create a team of experts who understand electronics, kernel development, operating system design, application code, user experience, and user interface design. This entire team also needs to understand and believe in the mission, so the entire team is dedicated to the same cause and developing toward the common goal of full stack freedom and the best security practices.
The Schematics
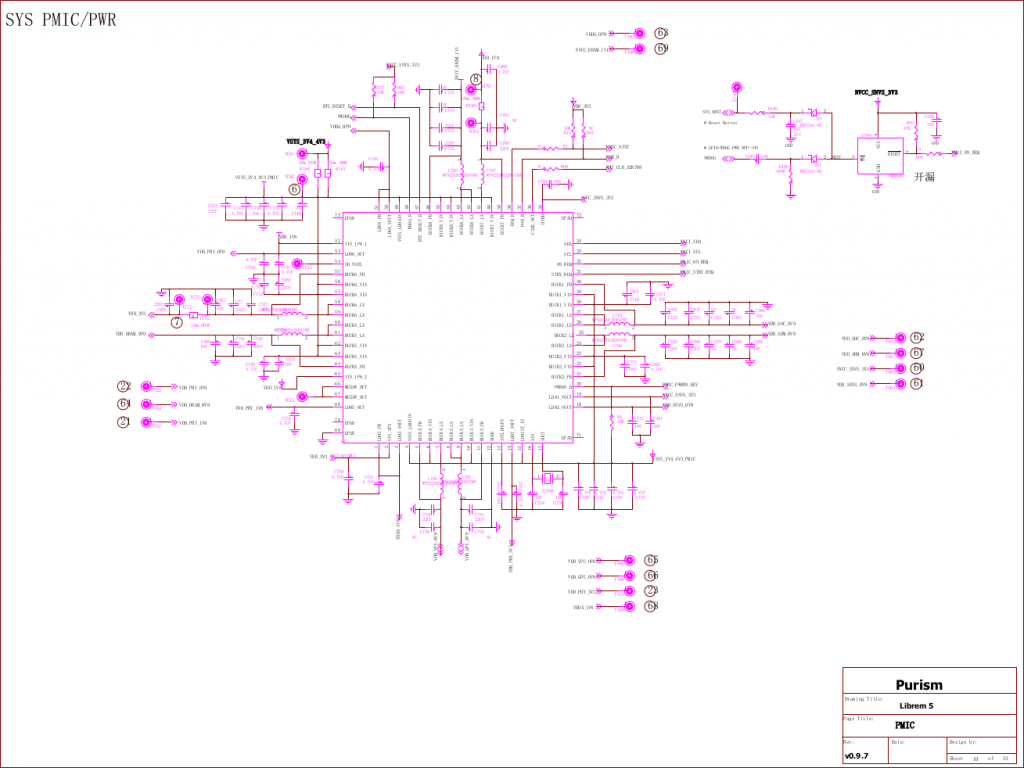
You need to author, oversee, have the source, and control the entire electrical engineering process. Having authorship control of the schematics means every trace, every resistor, every capacitor, every integrated circuit is confirmed to align with the team and the vision behind the entity.
The Hardware

Creating the most secure phone requires isolation of components. It requires separating out the radios (Cellular Baseband and WiFi/Bluetooth) from the main CPU and from the Memory. It requires to release all the source code that touches the CPU so it can be verified and audited to not have any backdoors or malicious code (unreleased source code is malware by definition and should be treated as such). Making the most secure phone would need to run hardware chips proven to have the best security available, it would require to be made recently, it would require to have long-term support from the chip makers, it would require having the ability to easily hardware kill-switch radios, cameras, microphones, and sensors. It should also look and feel like all other phones on the market, meaning a black-slate touch screen with applications for common use cases. It should offer a solid foundation to build on that is the most solid phone architecture that can offer virtualization, multiple fast cores, and a full-stack development team behind it.
The Kernel (and Bootloader)
The Linux kernel (and bootloader) must be under the complete control of the owner not the manufacturer or any other 3rd party. It should track the latest mainline Linux kernel to make sure it is current, fast, patched, secure, and offers the best developmental future for securing the phone.
The Operating System
To create the most secure operating system, you must start with a foundation that is freedom respecting – meaning all the source is released by people and organizations that fully respect that fact – and then make sure all parts that build on that foundation are equally strong in its alignment to security and user ownership. A great measurement of this is the gold standard of freedom for an operating system, the Free Software Foundation endorsement, from there you can adhere to the strictness in all software that enters the operating system and touches the main CPU. This ensures that 100% of the operating system is under the control of the person, business entity, or OS team within a large enterprise or government agency. By having complete control it means they can do with it what they desire, including adding things specific to their needs without having to jailbreak, root, or break license agreements.
The Software
All software that is included in the Operating System must also have all the source code released, it must ensure there are no backdoors, malicious data calls, and confirm that the owner of the device has complete control of the device. Furthermore, the software should advance reproducible builds, so people can rest-assured that the software running is binary matched against others who also build and confirm the software has not been tampered with.
The Software Store
Just like the core phone appliactions, all software in the Software Store, must align with the security and freedom requirement of releasing the software source code. Allowing your organization to audit every aspect of your ecosystem, guaranteeing the most hardened secure phone.
The Longevity of a Secure Phone
An often not-talked-about threat to phones and secure phones is the longevity of the hardware, software, and services; rather than being a rip-and-replace every year or two, having the most secure phone that also has a lifespan from the hardware chip makers through the operating system measured in decades is ideal to marry the security requirements with a long term support of a device used in the most secure locations and use cases on earth.
The Most Secure Phone
Making the most secure phone is not just slapping some monitoring tool onto proprietary rights stripping OSes. It is not believing the marketing terms of “We use encryption; we are secure; or we care about privacy.” advocated by big-tech firms. It is recognizing that you have to start at the foundational level of the business, own and control the schematics, manufacturing, hardware selection, kernel, operating system, software, software store, and offer that. Only then can you truly claim to be the most secure phone for businesses, enterprises, governments, and all of society.
Discover the Librem 5
Purism believes building the Librem 5 is just one step on the road to launching a digital rights movement, where we—the-people stand up for our digital rights, where we place the control of your data and your family’s data back where it belongs: in your own hands.
Recent Posts
Related Content
- PureOS Crimson Development Report: November 2025
- PureOS Crimson Development Report: October 2025
- Consent On Everything?
- 60 Minutes Uncovers Hacks on America’s Infrastructure
- Purism CEO Todd Weaver: U.S.-Made Liberty Phone Proves Domestic Tech Manufacturing Is Possible—and Competitive


