Defending Against Spyware Like Pegasus
Purism
Latest posts by Purism (see all)
- A Quarter Century After Cyberselfish, Big Tech Proves Borsook Right - December 20, 2025
- PureOS Crimson Development Report: November 2025 - December 15, 2025
- Purism Liberty Phone Exists vs. Delayed T1 Phone - December 10, 2025
This has been a busy week for security news, but perhaps the most significant security and privacy story to break this week (if not this year), is about how NSO Group’s Pegasus spyware has been used by a number of governments to infect and spy on journalists and activists and even heads of state by sending an invisible, silent attack to their iPhone that requires no user interaction. This attack works even on new, fully-patched phones, and once the phone is compromised, the attacker has full remote control over the phone including access to the file system, location, and microphone and cameras.
What’s particularly scary about spyware in general, and is true for Pegasus as well, is that victims have no indication they’ve been compromised. Due to how locked down the iPhone is from the end user, detecting Pegasus in particular requires expert forensics techniques. This has left many at-risk iPhone users wondering whether they too are compromised and if so, what do they do?
Ambulance Chasing
The infosec industry is prone to ambulance chasing. After every major security incident you can count on your Inbox filling with emails from vendors claiming they could have stopped it. As a result I typically wait weeks if not months after a security incident to publish my thoughts so I can avoid even the appearance of ambulance chasing.
However, we have had customers ask us about this incident and whether our hardware would be vulnerable, so instead of writing a lot of individual replies, I figured it was better to go ahead and publish something on how we approach defending against spyware in general. Even though Pegasus doesn’t work on our products, our defense would apply to it and any other spyware that was ported to our platform.
Outsourced Security
Most vendors want all security outsourced to them, so you become fully dependent on and locked into them for security (and everything else). In the name of security, phone vendors already have remote control over their customers’ phones and some also use this capability to spy on their customers. When attackers discover new ways to bypass those defenses, vendors respond by locking the device down further, not just from attackers, but from users.
Vendors believe they must protect users from themselves and so while people may believe their phone is in an elite gated community, the reality is closer to a digital nursing home. When something inevitably goes wrong (like with Pegasus) the user is left without any options except to wait for the vendor to save them. This is all-or-nothing security, and any attempt by the user to get more control over their hardware–if the vendor allows it–means disabling vendor security almost entirely.
A Unique Defense
Our defense is unique in the industry, because we design our products to give the customer control over their own security. This focus on user control means we reject a lot of security measures the industry adopts that give vendors control and either adapt those measures or replace them with others that achieve a similar level of security while letting the user hold the keys. We think the right design balances security, privacy and freedom–our three-legged stool–because we believe you must have all three to have any.
The most obvious forms of this customer-focused design are the hardware kill switches in our phone and laptop. That way, even if spyware were to get past our other defenses, the user has control over the last line of defense and can physically disable the microphone, camera, WiFi and the cellular modem whenever they want to know for sure they have privacy.

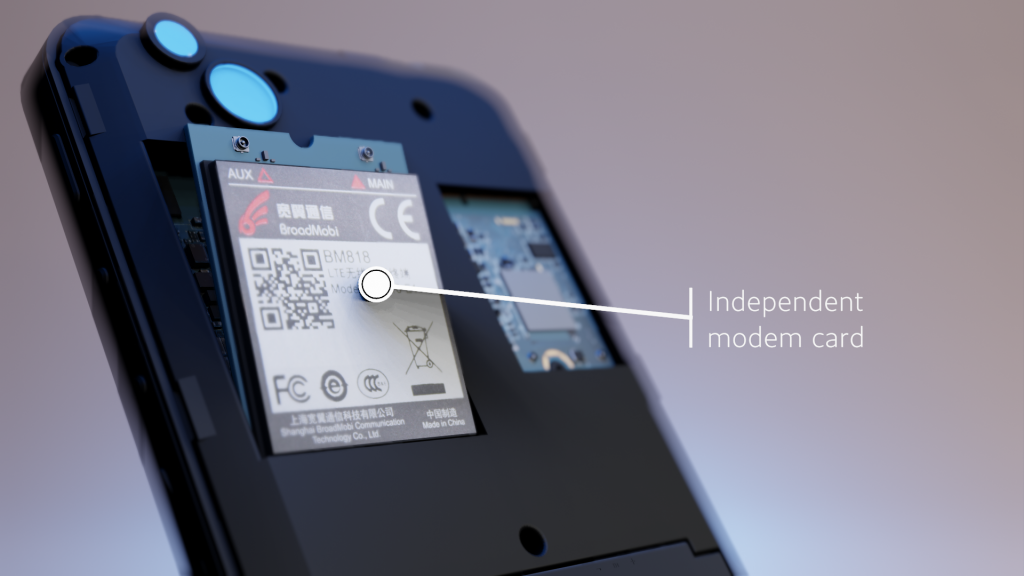
Due to how we designed the Librem 5, the cellular modem is independent from the main CPU and so doesn’t have to be on whenever the phone is on. One way that spyware tracks people is through the cellular towers they connect to. Disabling the modem in software using “airplane mode” is something spyware might be able to block, but by being able to turn the modem off with a kill switch, you know for sure it can’t be tracked when you need extra privacy.
Of course this isn’t just a security measure for spies, journalists and activists. Regular people are victims of spyware all the time from controlling spouses or angry exes. Even if you don’t face an immediate threat, hardware kill switches are so fast and easy to use, that many people end up disabling the microphone and camera by default and only switch them on when they need to use them. This approach is even more common with our laptops (where spyware is an equal threat), since the average person only uses the webcam and microphone when they are on a video call.

Lockdown Mode
On our Librem 5 phone, we go a step further, because phones have so many more sensors than your average computer. By disabling all three hardware kill switches you can enter “lockdown mode” which disables all other active and passive sensors on the device such as the GPS and accelerometer. This helps protect against spyware that might log GPS coordinates even if the user disables location services in software. We also designed the Librem 5 so that the WiFi and cellular modems, along with the battery, were removable, so you have options even if you don’t trust our hardware kill switches.
The Spy Within
Another problem phones face with spyware is that the entire platform has been designed to collect user data. Security ends up focusing on how to enable the vendor to collect the data without letting anyone else snoop on it. It’s not much different from the current debate over encryption backdoors. There’s no such thing as a backdoor only the “good guys” can access, and the same is true for data collection.
Some vendors realize privacy is a marketing advantage, and so they now alert you when other apps try to snoop on you, yet their tools conveniently never alert you to their own snooping. Even when you explicitly opt out, data collection continues. According to one research paper:
We find that even when minimally configured and the handset is idle both iOS and Google Android share data with Apple/Google on average every 4.5 mins. The phone IMEI, hardware serial number, SIM serial number and IMSI, handset phone number etc. are shared with Apple and Google. Both iOS and Google Android transmit telemetry, despite the user explicitly opting out of this.
The best way to protect user data is not to collect it in the first place, and that’s the fundamental approach we’ve taken with our software. We have no incentive to collect user data and in fact it runs counter to our Social Purpose. This frees us up to make data collection in general more difficult not just for attackers but for us as well. Since our products run Free Software, you don’t have to take our word for it either–you can audit all our claims and see what we are doing under the hood.
My post Snitching on Phones that Snitch on You describes many of the ways we protect users from data collection, and includes a section on how to use the OpenSnitch tool to monitor all traffic leaving your device so you can more easily detect when spyware is trying to phone home.
Defend Your Castle
Security measures on most phones are focused more on keeping the customer in and competitors out. Keeping attackers out is a convenient side-effect and makes for good marketing. Pegasus illustrates that even with talented, well-funded security engineers, outsourcing all security, trust, and control to the vendor has its limitations. In the end, the best defense against spyware is for the user to have control over the hardware, so they can switch it off, and over the software so they can inspect it. Your phone is your castle and you should be allowed to defend it.
Purism Products and Availability Chart
| Model | Status | Lead Time | ||
|---|---|---|---|---|
 | Librem Key (Made in USA) | In Stock ($59+) | 10 business days | |
 | Liberty Phone (Made in USA Electronics) | In Stock ($1,999+) 4GB/128GB | 10 business days | |
 | Librem 5 | In Stock ($799+) 3GB/32GB | 10 business days | |
 | Librem 11 | In Stock ($999+) 8GB/1TB | 6+ weeks | |
 | Librem 14 | Out of stock | New Version in Development | |
 | Librem Mini | Out of stock | New Version in Development | |
 | Librem Server | In Stock ($2,999+) | 45 business days | |
 | Librem PQC Encryptor | Available Now, contact sales@puri.sm | 90 business days | |
 | Librem PQC Comms Server | Available Now, contact sales@puri.sm | 90 business days |
Recent Posts
Related Content
- A Quarter Century After Cyberselfish, Big Tech Proves Borsook Right
- PureOS Crimson Development Report: November 2025
- PureOS Crimson Development Report: October 2025
- Landfall: A Case Study in Commercial Spyware
- Librem PQC Encryptor: Future‑Proofing Against Both SS7 and Quantum


