DHS Security Report: Data Security & Privacy At The OS Level
Latest posts by Rex M. Lee (see all)
Data security and end user privacy requires focusing on the operating system (OS) that supports smartphones, tablet PCs, connected products, IoT/IIoT devices, wearable tech, and PCs.
The Problem- Leaky Operating Systems and Intrusive Apps
Intrusive app and social media developers, plus nation-state hackers, know that one of the largest gateways to the smartphone or PC end user is through the operating system which means that Google, Apple, and Microsoft are selling access to their OS end users to intrusive app and social media developers worldwide.
Unfortunately, today’s connected products which include smartphones and PCs are not private nor secure forms of telecommunications or computing due to popular operating systems that support uncontrollable preinstalled apps and social media platforms designed to support surveillance and data mining technologies.
Popular mobile operating systems that include Android and Apple iOS can be described as “Leaky” because these operating systems are intentionally designed to enable preinstalled app developers to conduct surveillance on the OS end user while data mining the customer for profit 24×7/365 days per year.
As a matter of fact, operating systems supported by intrusive preinstalled apps pose massive security and privacy threats to the OS end user, plus the end user’s employer.
Some security experts will contest that mobile device management (MDM) platforms can protect OS end users from intrusive apps and social media platforms. This is partially true when speaking about additional 3rd party apps the OS end user downloads from app stores such as Google Play or Apple App Store. However, MDM platforms will not protect the OS end user from uncontrollable preinstalled surveillance and data mining apps developed by the OS developer, plus their preinstalled app developer partners according to an admission made by T-Mobile per a formal consumer complaint filed with the FCC by a T-Mobile customer (FCC Complaint#423849).
Consequently, Verizon admitted this fact as well regarding a formal request from a customer to purchase a secure and private smartphone or tablet PC to use within the defense/critical infrastructure industries.
The Department of Homeland Security Science and Technology published a Study on Mobile Device Security in 2017 that describes intrusive apps as “Malicious” apps enabling the developer to conduct audio, video, and physical surveillance (see Figure 2/DHS Study) on Android and iOS end users by way of hardware such as the camera and microphone, plus sensors such as GPS, NFC Tags, Bluetooth, and the accelerometer.
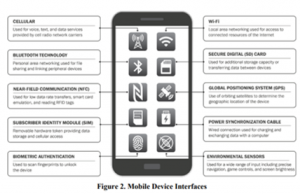
“Surreptitious Eavesdropping. Some malicious apps are capable of quietly accessing device sensors to eavesdrop or photograph the user or others.”- DHS S&T Study on Mobile Device Security/Page 34
A single intrusive application enables the developer to collect over 5,000 highly confidential data points associated with the OS end user’s business, personal, medical, legal, and employment information since the surveillance and data mining conducted by the app developer is indiscriminate.
“Apps that Gather Privacy-Sensitive Information. These are malicious apps that can collect information such as device persistent identifiers, device location, list of installed applications, contact lists, call logs, calendar data, or text messages without adequate consent of the user”- DHS S&T Study on Mobile Device Security/Page 34
Due to security and privacy threats posed by intrusive apps, numerous governments around the world are banning the use of intrusive apps which can be described as “Legal Malware”.
This means that the OS end user’s highly confidential and protected business information is also being collected by the OS developer, plus the app developers which many compete in numerous industries worldwide such as Alphabet (Google), Tencent (WeChat), Meta (Facebook), and so on.
Business end users of apps that support the oppressive operating systems are inadvertently exposing highly confidential and protected information to numerous unauthorized third parties, including existing or future business competitors pending the industries the end user works within.
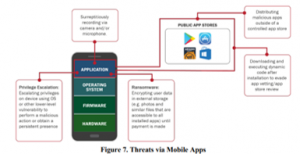
Intrusive apps can also be used to launch numerous attacks (see figure 7/DHS Study) on networks that include Man-in-the-Middle, Distributed Denial of Service, and Ransomware Attacks.
The Solution- Smartphones and PCs Supported by PureOS
Purism has developed an operating system, PureOS, that provides data security resulting in OS end user privacy.
PureOS is a fully free, auditable and open-source Linux operating system that is not based on the Android OS nor Apple iOS.
PureOS supports smartphones, laptop PCs, and servers manufactured by Purism.
The Librem 5 USA smartphone with made in the USA electronics for the ultimate supply chain security runs PureOS.
The Librem 14 (“The Road Warrior”) laptop PC supports numerous security features such as PureBoot which provides firmware tamper protection and runs PureOS.
Purism offers Anti-Interdiction Services that support product delivery security and the Librem Key which is a USB security token to make encryption, key management, and tamper detection convenient and secure.
PureOS supports true convergence which means PureOS fully supports a wide array of hardware form factors such as the Librem 5 USA smartphone, the Lapdock to turn the Librem 5 phone into a laptop, the Librem Mini PC, and the Librem 14 laptop putting the product owner in full control over their security and privacy.
Purism also provides custom development to support out-of-scope security needs for government, military, law enforcement, and businesses who are required to use smartphones, laptops, servers, and PCs that are the most secure devices available today.
Purism can even help you decouple from big tech through decentralization services hosted within your own domain.
Contact us for more information at sales@puri.sm
Purism Products and Availability Chart
| Model | Status | Lead Time | ||
|---|---|---|---|---|
 | Librem Key (Made in USA) | In Stock ($59+) | 10 business days | |
 | Liberty Phone (Made in USA Electronics) | In Stock ($1,999+) 4GB/128GB | 10 business days | |
 | Librem 5 | In Stock ($799+) 3GB/32GB | 10 business days | |
 | Librem 11 | In Stock ($999+) 8GB/1TB | 6+ weeks | |
 | Librem 14 | Out of stock | New Version in Development | |
 | Librem Mini | Out of stock | New Version in Development | |
 | Librem Server | In Stock ($2,999+) | 45 business days | |
 | Librem PQC Encryptor | Available Now, contact sales@puri.sm | 90 business days | |
 | Librem PQC Comms Server | Available Now, contact sales@puri.sm | 90 business days |
Recent Posts
Related Content
- A Quarter Century After Cyberselfish, Big Tech Proves Borsook Right
- PureOS Crimson Development Report: November 2025
- Purism Liberty Phone Exists vs. Delayed T1 Phone
- PureOS Crimson Development Report: October 2025
- Landfall: A Case Study in Commercial Spyware


