Stay Safe from BMC Tampering
Latest posts by Jonathon Hall (see all)
- PureOS Crimson Development Report: November 2024 - December 16, 2024
- Purism’s PureBoot is Not Affected by UEFI Key Leaks (Again) - July 29, 2024
- From the Hackdesk: Librem 16 - May 30, 2024
Through June and July, AMI MegaRAC BMC firmware has been in the news owing to high-severity vulnerabilities that have existed for years but only recently come to light. Server hardware widely contains BMCs, and compromising one can give near-total control over the server. Many vendors shipped this firmware with their own branding.
But what exactly is a BMC, and what can we do to stay secure?
Baseboard Management Controller
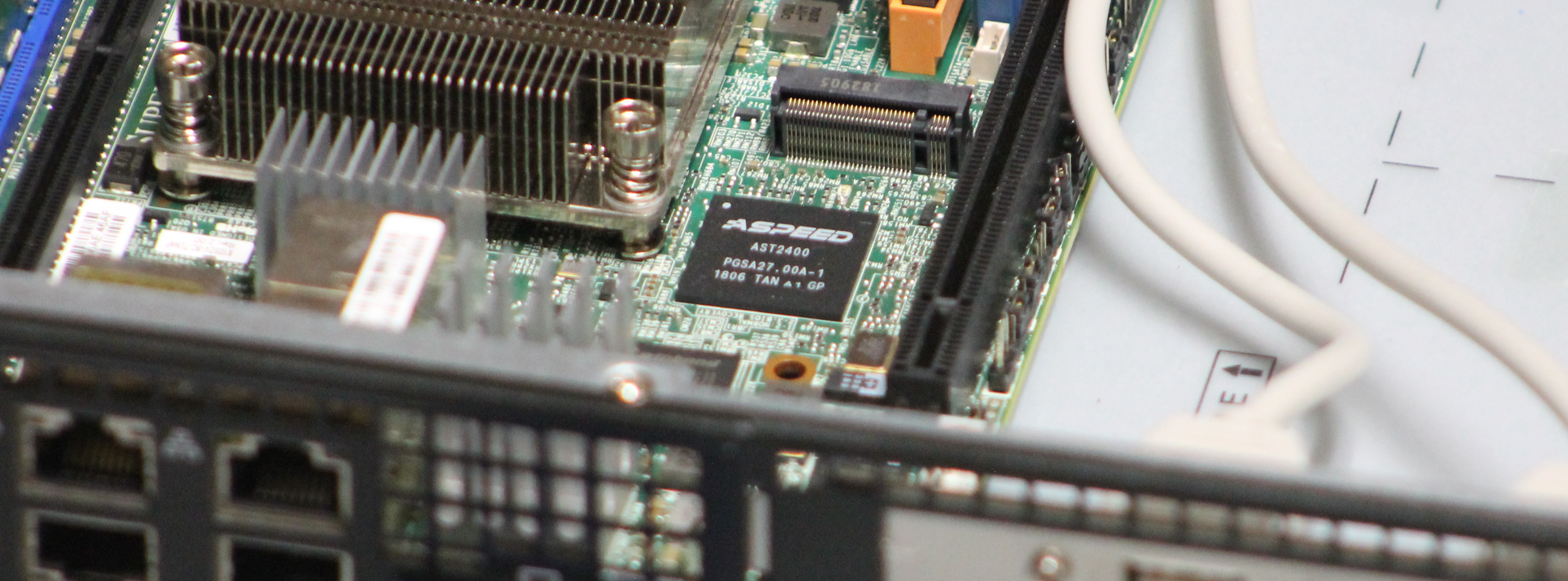
A BMC, or “Baseboard Management Controller”, manages a server remotely. Physical access to servers is typically tightly controlled (or at least very inconvenient). But like any computer, it could go offline, fail to boot, or otherwise misbehave. If this was your PC at home, you’d go sit down at the keyboard and monitor to troubleshoot it, and maybe reinstall the OS from USB, but on a server we want to do this remotely.
That’s where the BMC comes in. One of its key functions is to make the “physical” keyboard, monitor, and power button, available remotely over a web interface. Often, you can attach a local ISO as a virtual USB disk, and the remote system thinks it is a real USB disk. Remote serial ports and many other features are possible too.
All of this works if the OS’s networking is broken, or even if the entire OS is unbootable. The BMC may even be able to flash the system BIOS, allowing recovery from a failed flash or broken firmware. You may have done this before for virtual machines – the BMC brings remote management to physical systems.
The BMC is a second, smaller computer hanging off of the main computer. Much like the embedded controller in a laptop, it is in charge of powering on or off the main system. The BMC is always on when the server is plugged in, like the EC. It is a complete computer, commonly containing an ARM CPU, DRAM, and its own firmware.
Bring Many Connections
To provide all these features, the BMC connects to many buses from the main system. The BMC firmware fully controls some interfaces, while hardware functionality controls others.
- PCI Express: The BMC contains a PCIe video card. It stores the framebuffer in BMC memory as well as scanning it out to a physical monitor, if there is one. The BMC can observe the framebuffer and provide it over a network connection.
- LPC (“Low Pin Count”): The BMC can provide serial ports and snoop on POST codes from the main system.
- USB: The BMC acts as a USB keyboard, mouse, or storage device.
- SPI: The BMC may sit “between” the main system and its BIOS firmware chip, providing a way to flash the BIOS when the main system is offline.
- Ethernet: BMCs often can share the host’s physical network interface, eliminating an extra cable. If they use separate networks, the BMC may share its network interface to the host over USB.
The main system is unlikely to consider any of these buses to be security boundaries. The BMC has great power to lie about what is on the display, hide it from a physical monitor, or act as a malicious USB device.
Be Maximally Cautious
Purism disables BMC functionality on Librem Servers where possible. PureBoot, when combined with a Librem Key, authenticate the system firmware to you, which complicates any tampering attack.
Purism Products and Availability Chart
| Model | Status | Lead Time | ||
|---|---|---|---|---|
 | Librem Key (Made in USA) | In Stock ($59+) | 10 business days | |
 | Liberty Phone (Made in USA Electronics) | In Stock ($1,999+) 4GB/128GB | 10 business days | |
 | Librem 5 | In Stock ($799+) 3GB/32GB | 10 business days | |
 | Librem 11 | In Stock ($999+) 8GB/1TB | 6+ weeks | |
 | Librem 14 | Out of stock | New Version in Development | |
 | Librem Mini | Out of stock | New Version in Development | |
 | Librem Server | In Stock ($2,999+) | 45 business days | |
 | Librem PQC Encryptor | Available Now, contact sales@puri.sm | 90 business days | |
 | Librem PQC Comms Server | Available Now, contact sales@puri.sm | 90 business days |
Recent Posts
Related Content
- A Quarter Century After Cyberselfish, Big Tech Proves Borsook Right
- PureOS Crimson Development Report: November 2025
- PureOS Crimson Development Report: October 2025
- Landfall: A Case Study in Commercial Spyware
- Librem PQC Encryptor: Future‑Proofing Against Both SS7 and Quantum


